Chapter 6: Edge Security and Privacy
6. Edge Security and Privacy
6.1 Overview of Security Challenges in Edge Computing
From previous chapters, Edge Computing has shown that it is here to stay and it will keep rapidly growing throughout the years. However, Edge Computing has its own security challenges that have to be addressed, because it is not a perfect system. Edge Computing has many security challenges that have to be dealt with in order to keep data safe.
DDoS
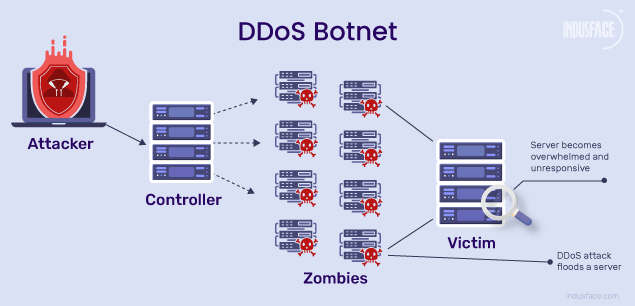
DDoS is a type of cyberattack in which an attacker aims to disrupt services provided by one or more servers based on distributed based on distributed resources such as a cluster of compromised Edge devices, which are also known as botnets. DDoS attacks occur when an attacker persistently sends streams of packets to a victim from compromised electronic devices, which causes the hardware resources of the victim to be quickly exhausted by handling these malicious packets and can no longer process any legitimate request on time. There are two kinds of DDoS attacks: Flooding-based and Zero-day DDoS attacks.
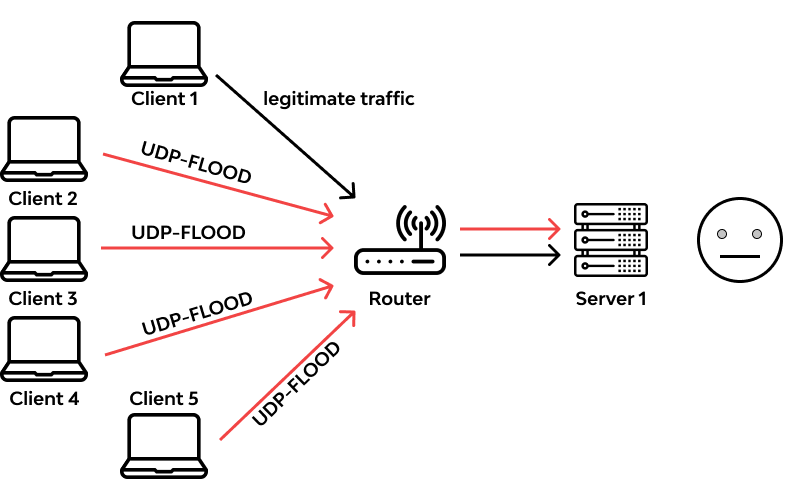
Flooding-based DDoS attacks are a type of of DDoS attacks aiming to shut down normal service of a server based on large amount of flooded malformed or malicious network packets and are mainly classified as UDP flooding, ICMP flooding, SYN flooding, ping of death (PoD), HTTP flooding, and Slowloris.
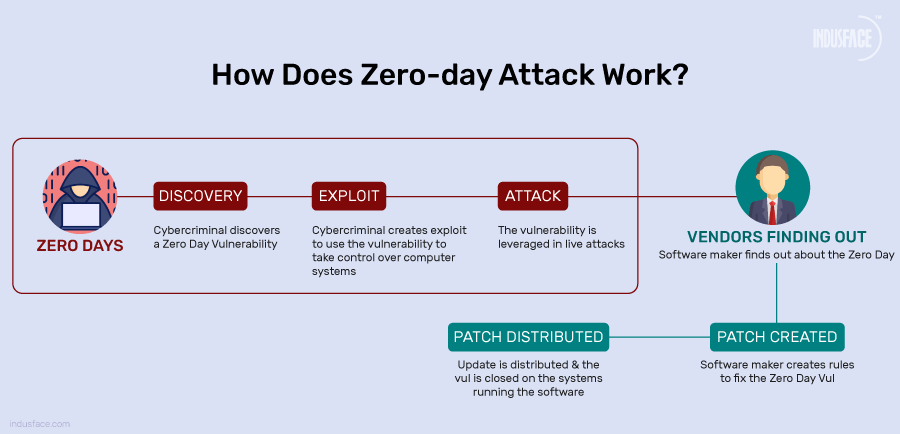
Zero-Day DDoS attacks are when an attacker must find an unknown vulnerability in a piece of code running on the target Edge server or device, which can cause memory corruption and finally result in a service shutdown. For example, newly built Edge servers could have code vulnerabilities, such as a hanging pointers or stack overflows, and an attacker can abuse those vulnerabilities in order to cause the Edge servers or devices to overload due to memory issues and shut down.
Side-Channel Attacks
Side-Channel Attacks happen when an attacker constantly obtains certain side-channel information, like using public information that is not privately-sensitive for a user, from the target edge computing infrastructure and then feeds it into specific algorithms or machine learning models that outputs the desired sensitive information. There are three kinds of Side-Channel attacks: attacks exploiting communication channels, attacks exploiting power consumption, and attacks exploiting smartphone-based channels.
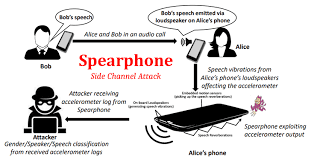
Attacks exploiting communication channels are when an attacker can use a malicious node, that doesn't have to be an edge server or device, in order to exploit communication channels and uses the node to continuously sniff the network traces and wishes to extract sensitive information out of them. Attacks exploiting power consumption are when attackers use smart meters and oscilloscopes in order to measure the power consumption of a system since it carries information related to either the device that consumes the energy as different devices have different power. Attacks exploiting smartphone-based channels are when attackers exploit vulnerabilities using /proc and smartphone embedded sensors due to how sensors can leak information and send malware to the user that they can install but disguised as something important and attack /proc.
Malware Injection
Malware Injection is when an attacker injects malicious code, or malware, into edge devices or servers and is classified as either server-side or device-side injections. Server-side injections are separated into four types: SQL, XSS, CSRF and SSRF, and XML. Device-side injection is when an attacker injects the malware directly into IoT devices since IoT devices are highly heterogeneous, so an attacker can physically inject or use third-party malicious libraries that are powerful and less likely to get detected.
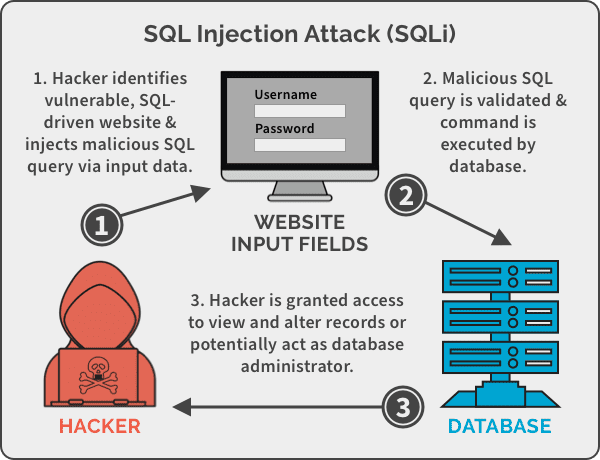
SQL injection is a code injection technique that attackers can use in order to destroy back-end databases by using the SQL query and escape sequences to trick the server into thinking the code is valid. XSS injection is a client-side attack in which an attacker injects malicious code into data content, which can be accessed and executed automatically by the servers. CSRF injection is an attack in which an end user is forced to execute unwanted actions through Web applications. SSRF injection is an attack in which Edge servers are abused to read or alter the internal resources. XML injection is an attack which an attacker intercepts an XML message and edits with malicious code so that it is sent to the Edge servers using Simple Object Access Protocol (SOAP).