Chapter 6: Edge Security and Privacy
6. Edge Security and Privacy[edit]
6.1 Overview of Security Challenges in Edge Computing[edit]
From previous chapters, Edge Computing has shown that it is here to stay and it will keep rapidly growing throughout the years. However, Edge Computing has its own security challenges that have to be addressed, because it is not a perfect system. Edge Computing has many security challenges that have to be dealt with in order to keep data safe. In this section, we will be talking about the different kinds of attacks that can happen on an Edge server or device, as how they are able to do this.
DDoS[edit]
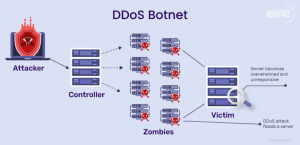
DDoS is a type of cyberattack in which an attacker aims to disrupt services provided by one or more servers based on distributed based on distributed resources such as a cluster of compromised Edge devices, which are also known as botnets.
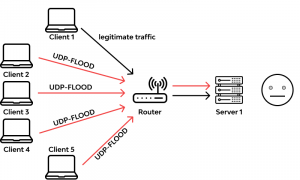
DDoS attacks occur when an attacker persistently sends streams of packets to a victim from compromised electronic devices, which causes the hardware resources of the victim to be quickly exhausted by handling these malicious packets and can no longer process any legitimate request on time. There are two kinds of DDoS attacks: Flooding-based and Zero-day DDoS attacks.
Flooding-based DDoS attacks are a type of of DDoS attacks aiming to shut down normal service of a server based on large amount of flooded malformed or malicious network packets and are mainly classified as UDP flooding, ICMP flooding, SYN flooding, ping of death (PoD), HTTP flooding, and Slowloris.
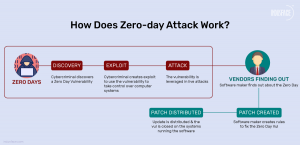
Zero-Day DDoS attacks are when an attacker must find an unknown vulnerability in a piece of code running on the target Edge server or device, which can cause memory corruption and finally result in a service shutdown. For example, newly built Edge servers could have code vulnerabilities, such as a hanging pointers or stack overflows, and an attacker can abuse those vulnerabilities in order to cause the Edge servers or devices to overload due to memory issues and shut down.
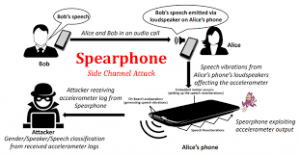
Side-Channel Attacks[edit]
Side-Channel Attacks happen when an attacker constantly obtains certain side-channel information, like using public information that is not privately-sensitive for a user, from the target edge computing infrastructure and then feeds it into specific algorithms or machine learning models that outputs the desired sensitive information. There are three kinds of Side-Channel attacks: attacks exploiting communication channels, attacks exploiting power consumption, and attacks exploiting smartphone-based channels.
- Attacks exploiting communication channels are when an attacker can use a malicious node, that doesn't have to be an edge server or device, in order to exploit communication channels and uses the node to continuously sniff the network traces and wishes to extract sensitive information out of them.
- Attacks exploiting power consumption are when attackers use smart meters and oscilloscopes in order to measure the power consumption of a system since it carries information related to either the device that consumes the energy as different devices have different power.
- Attacks exploiting smartphone-based channels are when attackers exploit vulnerabilities using /proc and smartphone embedded sensors due to how sensors can leak information and send malware to the user that they can install but disguised as something important and attack /proc.
Malware Injection[edit]
Malware Injection is when an attacker injects malicious code, or malware, into edge devices or servers and is classified as either device-side or server-side injections.
Device-side injection is when an attacker injects the malware directly into IoT devices since IoT devices are highly heterogeneous, so an attacker can physically inject or use third-party malicious libraries that are powerful and less likely to get detected.
Server-side injections are separated into four types: SQL, XSS, CSRF and SSRF, and XML.
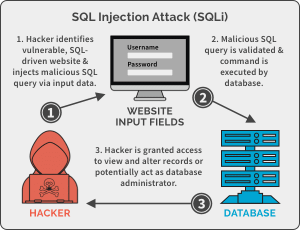
- SQL injection is a code injection technique that attackers can use in order to destroy back-end databases by using the SQL query and escape sequences to trick the server into thinking the code is valid.
- XSS injection is a client-side attack in which an attacker injects malicious code into data content, which can be accessed and executed automatically by the servers.
- CSRF injection is an attack in which an end user is forced to execute unwanted actions through Web applications and SSRF injection is an attack in which Edge servers are abused to read or alter the internal resources.
- XML injection is an attack which an attacker intercepts an XML message and edits with malicious code so that it is sent to the Edge servers using Simple Object Access Protocol (SOAP).
Authorization and Authentication Attacks[edit]
When these attacks happen, an attacker can bypass authentication processes and gain unauthorized access by using four techniques: dictionary attacks, attacks exploiting vulnerabilities in authorization protocols, attacks exploiting vulnerabilities in authorization protocols, and overprivileged attacks.
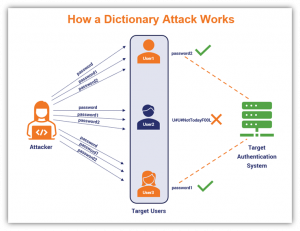
- Dictionary attack is when an attacker possesses a dictionary containing the most used credentials or passwords and inputs all possible entries in this dictionary in order to brute force a match.
- Attacks exploiting vulnerabilities in authorization protocols are when attackers look for design flaws in how authentication protocols are being used, like finding vulnerabilities in WPA2 or WPA3 protocols which can give an attacker messages that have encrypted information. They can also use 4G or 5G vulnerabilities in order to find a person's location and inject fabricated paging messages to mess with them and gain more information.
- Attacks exploiting vulnerabilities in authorization protocols are when attackers look for flaws in how authorization protocols are designed, such as an attacker using vulnerabilities in OAuth single sign-in which let them access victims personal information without authorization.
- Overprivileged attacks are when attackers are able to develop malicious apps that can do things that they do not have permission to do without needing to authenticate, such as changing door pins and setting off fire alarms in a house.
How are attackers able to perform these attacks?[edit]
Attackers are able to attack Edge devices or servers using different attack techniques, but it is more than just that. Attackers are able to abuse vulnerabilities and flaws in the Edge systems, specifically protocol-level design flaws, implementation-level flaws, code-level vulnerabilities, data correlations, and lacking in fine-grained access controls.
- Protocol-level design flaws are caused by many protocols edge computing having adopted design flaws due to their designers mainly focus on utility and user experience rather than not providing security as well.
- Implementation-level flaws are logic flaws that can cause security strength to decrease significantly after being proved that it was strictly secure on paper, because developers may misunderstand the foundations of the protocol and migrating a protocol from other platforms to the edge computing platform may cause adaptivity inconsistency.
- Code-level vulnerabilities can be system bugs that cause memory failure or corruptness, like stack or heap overflow, and can be caused when a person is programming millions of lines of code but leaves something like a dangling pointer.
- Data correlations is caused when there could be hidden correlations between sensitive and insensitive data that edge produces that might not be straightforward to notice, which an attack can abuse using side-channels.
- Lacking in fine-grained access controls means that Edge computing systems cannot implement fine-grained access controls, because it cannot be adapted to edge computing due to the more complex and fine-grained permissions scenarios, making it easier to attack edge systems.
Overall, the Edge security challenges can be avoided if there was more attention to the potential vulnerabilities or flaws. In the next sections, the content that will be discussed is about data privacy on Edge systems, security protocols that Edge systems use to combat attacks on their systems, and real cases about actual security breaches that happened on the edge.
6.2 Data Privacy and Compliance in Edge Applications[edit]
Privacy Issues in Fog Computing[edit]
Attack Vectors[edit]
Below are some of the major attack vectors that plague existing edge and fog networks.
- Forgery
- Forgery is a security threat where the attacker copies someone else's identities and behavior by producing fake information. This is a serious issue that degrades existing network resources for everyone in the network.
- Tampering
- Attackers alter data that is to be sent to other websites. This is difficult to detect since users in an edge environment are mobile and we can't differentiate if the data has been tampered with or anomalous behavior is due to packet loss.
- Spam
- Attackers send fake information that overwhelms the processing power of the edge devices. Similar to DoS, on a smaller scale.
- Sybil
- Attackers fake identity to control the performance of edge network. Falsifying their identity allows them to create fake crowdsensing reports, which affects the reliability of the whole network.
- Jamming
- Attackers generate large amounts of packets to jam transmission channels and occupy important resources
- Eavesdropping
- Attackers listen to confidential data of genuine users from transmission channel by pretending to be a part of the network
- Man in the Middle (MITM)
- MITM is a type of cyberattack where the attacker not only eavesdrops on communication between two devices, but also modifies the payload for destructive payloads.
- Collusion
- Multiple groups band together to mislead fog nodes
- Impersonation
- Attacker acts as real server to trick users to steal all their data
Privacy Issues in Fog Computing[edit]
- User privacy
- Fog computing contains large number of IoT devices that are inter-connected via sensors, which generate sensitive data and transmit to fog nodes for processing. This raises the question of guaranteeing user privacy in the case of a breach in a part of the system.
- Data Privacy
- User data can be exposed to network attacker who is trying to steam user's personal data from the transmission medium or relay nodes
- Usage privacy
- User's usage patterns for fog computing usage may get leaked. If the intruder knows when user is accessing the channel, they may target the user's confidential information when the user is not using the channel.
- Location Privacy
- Intruders accessing nodes' location information poses a risk for the user both physically and on the network.
- Network Privacy
- Since most fog networks are connected over wireless networks, which are relatively insecure, this also poses a ever-present security risk for users. Moreover, maintenance of fog nodes on wireless networks is also challenging since they are present at edge of internet. Both these factors expand the attack surface which makes it more likely for a breach to occur
Security and Privacy issues for edge computing[edit]
- nodes of edge connected to large number of IoT
- these have limited resources
- heterogeneous internal components
- Key management for ensuring privacy of data is difficult
Issues[edit]
- Edge nodes are near to users which makes large amount of sensitive data, which might be stolen
- Edge computing possess low network resources so doesn't support expensive encryption algos
- Edge environment consists of dynamic env which is changing, which allows attackers multiple ways to join the network
Also difficult to create securiy rules for a changing network
Attacks[edit]
- Eavesdropping
- Monitor channel to steal data
- DDoS
- interrupt normal services provided by different servers
- Data Tampering
- Attacker can alter the data transmitted over comm channel
- False data injection
- Attacker injects false code in network which brings all data to the attacker
- Physical attack
- Physical protection of edge infra is weak, which allows attackers to compromise the physical locations of edge devices.
- Rogue gateway
- inject large amounts of traffic into edge network infra, similar to MITM
Privacy issues in edge computing[edit]
- weak security techniques for system protection
- unsafe communication between devices
- difficult recovery and data backup
- no specific pattern of update reception
- lack of proper network visibility
- lack of user's selective data collection
Countermeasures for Fog Computing[edit]
- Efficient encryption techniques
- Allows for resource constrained edge devices to encrypt communcations with complex algorithms
- Decoy technique
- Authenticate data of user present the computing network by replacing original information with fake information that is provided to attackers
When breached, the attackers find the decoy files
- Intrusion detection system
- Detect and protect from attacks including DoS, insider attackers, port scanning attacks, flooding attacks on virtual machine, MITM
- Blockchain security for fog computing
- Blockchain is a way to cryptographically ensure the validity of a system while simultaneously increasing it's security. Using blockchain for edge computing reduces single point failure, increases network security and helps with tracking node status effectively.
6.3 Security Protocols and Frameworks for Edge Systems[edit]
Edge computing systems are characterized by decentralization, heterogeneous environments, limited computational resources, and physical exposure of devices. These unique properties necessitate tailored security protocols and robust architectural frameworks to ensure confidentiality, integrity, and availability of data and services. This section systematically outlines the foundational components required to secure edge computing deployments.
Secure Communication Protocols and Data Protection[edit]
Effective data protection in edge environments hinges on secure, low-latency communication channels and mechanisms to safeguard data both in transit and at rest.
Transport Layer Security (TLS 1.3) and Datagram TLS (DTLS): These are cryptographic protocols that provide end-to-end encryption for TCP and UDP traffic, respectively. TLS 1.3 offers faster handshakes and improved privacy by encrypting more metadata.
Virtual Private Networks (VPNs): VPN tunnels are commonly used to establish secure connections between remote edge devices and central cloud services, providing confidentiality over public networks.
Encrypted MQTT: MQTT, a popular protocol in IoT environments, can be secured using TLS to enable safe, publish-subscribe messaging patterns across edge nodes.
Data-at-Rest Encryption: Sensitive sensor and user data stored on edge devices are encrypted using symmetric or asymmetric cryptographic algorithms. Secure key storage is often handled via hardware security modules (HSMs) or Trusted Platform Modules (TPMs).
Secure Data Disposal: Techniques like crypto-erasure, which delete encryption keys instead of data itself, ensure that obsolete or decommissioned data is irrecoverable.
Authentication and Access Control Mechanisms[edit]
Given the distributed and autonomous nature of edge devices, strong identity and access management (IAM) mechanisms are vital for secure operations.
Public Key Infrastructure (PKI) and Device Identity: Each edge device is provisioned with a unique cryptographic identity (certificates or keys), enabling mutual authentication and secure bootstrapping of trust.
Multi-Factor Authentication (MFA): Administrative access to edge systems incorporates multiple layers of verification, such as passwords, smart tokens, and biometrics.
Role-Based Access Control (RBAC): This mechanism limits access based on the user’s or device’s role, reducing the risk surface in case of a security breach.
Zero Trust Architecture (ZTA): Built on the principle of “never trust, always verify,” ZTA ensures that every user, device, or service must be continuously authenticated and authorized, regardless of location.
Decentralized Security via Blockchain Technologies[edit]
Blockchain introduces trust, transparency, and automation into the edge ecosystem by decentralizing control mechanisms.
Immutable Audit Logs: All system events such as device access, firmware updates, and data operations are logged immutably on the blockchain, ensuring accountability and traceability.
Smart Contract-Based Access Control: Instead of relying on a centralized access manager, blockchain-based smart contracts dynamically enforce access policies across multiple devices.
Firmware Integrity Verification: Blockchain can validate firmware updates cryptographically, allowing only signed and verified firmware to be deployed, thus preventing tampering.
Secure Multi-Party Data Exchange: Distributed ledger technology facilitates trustworthy data sharing between stakeholders and edge nodes while preserving data integrity and non-repudiation.
Network-Level Defenses and Segmentation[edit]
Isolating and defending network pathways is essential to minimizing the blast radius of potential cyber attacks.
Firewalls and Intrusion Prevention Systems (IPS): Positioned at network perimeters and gateways, these systems inspect traffic for known signatures and block malicious content.
AI-Driven Anomaly Detection: Machine learning models can analyze network traffic patterns, CPU load, and telemetry for deviations that may indicate an intrusion or system compromise.
Network Segmentation: Logical and physical segmentation of networks based on functionality or sensitivity (e.g., separating administrative controls from sensor traffic) restricts lateral movement during breaches.
AI and ML Frameworks for Security Automation[edit]
AI-based systems offer predictive, adaptive, and automated responses to evolving security threats in edge computing.
Behavioral Analytics and Surveillance: Machine learning algorithms monitor baseline device behavior and detect anomalies in real-time, flagging potential threats proactively.
Federated Learning: This privacy-preserving ML technique enables distributed model training across edge devices without transferring raw data to central servers, reducing the risk of data leakage.
Automated Incident Response: AI frameworks can isolate compromised nodes, halt suspicious data flows, and update firewall rules automatically based on threat analysis.
Collaborative Threat Intelligence: Edge devices can participate in a decentralized network to share real-time indicators of compromise (IOCs), enhancing system-wide threat awareness.
Emerging Trends and Future-Proofing Edge Security[edit]
As edge ecosystems evolve, so must their defenses. Several emerging trends are paving the way for more resilient and scalable security solutions.
Post-Quantum Cryptography (PQC): As quantum computing threatens current cryptographic standards, PQC algorithms are being explored to secure future edge environments against quantum-based attacks.
5G-Enabled Security Enhancements: 5G introduces capabilities like network slicing and low-latency identity management, enabling more secure, context-aware services at the edge.
Secure Access Service Edge (SASE): SASE converges networking and security functions into a single cloud-delivered service model, integrating secure web gateways, ZTA, and software-defined WAN (SD-WAN) into edge deployments.
6.4 Case Studies: Real-World Security Breaches[edit]
To further illustrate the edge computer security concepts, we will give a couple of short case studies where edge computing security plays a prevalent role, as well as some solutions:
Securing Egyptian VMSs Smart City Infrastructure[edit]
Over hundreds of thousands of these edge devices such as traffic sensors, surveillance cameras, smart lighting systems, and environmental monitors are deployed in an urban Smart City. We have on the `the city edge cloud' these instruments for real-time traffic flow management, public safety alarm, environmental monitoring with life supports among the green plants – in the area usually known as! This city suffered a massive blackout, when multiple traffic lights were compromised at the source which caused them to act irregularly: Not issuing signals, leading to gridlocks.
Challenges:[edit]
How were the traffic controllers found to be vulnerable? Meaning they hack the password hole punch so they can bypass the external username password and gain direct access to the temples of our data. Moreover, on some cameras, the public IP of that camera is exposed, making remote attack possible: it was obviously a disadvantage for them. The edge network stutters steps from one organization to the next, making it hard however much one tries to apply security policy uniformly, as whose department is solely responsible for a given thing?
Solutions Introduced:[edit]
- Net Separation
- The city designed its infrastructure with isolation zones; meaning traffic
systems are completely isolated from all other municipal services so if one zone is attacked all other zones of that type remain intact.
- Password Overhaul
- Each unit was provided with a complete rehash to change its default
passwords and other weak credentials to hardened unique passwords. Remote administrative access was only accepted with Multi-Factor Authentication.
- Embrace of a Zero Trust Model
- In this city, we employed a robust, Zero Trust model. A
central token service gives authorization to every device communication and does not assume the inherent trust of devices.
- Firmware Handling
- The OTA management system required by installation ensures known
exploits like traffic light management are repaired when discovered. Firmware cannot be updated at weaker sites as the assumption is it is regularly updated.
- AI-based IDS Deployment
- An AI-based IDS at a traffic control center learns about every
equipment normal behavior going on at this session (like how frequently commands are sent out for lighting systems) generate alerts, activate promise lockdowns any time an abnormal behavior appears Mechanisms for rapid dissemination throughout the city.
Outcome:[edit]
As a result of the proactive settings, these attempts were quickly identified and contained, with a limited impact on operations. For example, a virus event that targeted digital kiosks was contained through micro-segmentation and AI detection mechanisms that quickly isolated and as such quarantined the attack. It led to enhanced overall resilience of this intelligent city — its citizens’ trust in IoT services is continually getting better.
IIOT (INDUSTRIAL IOT) IN MANUFACTURING[edit]
The production floor of a manufacturing company has integrated an IIoT system that is edge- based. Sensors associated with the machinery connect to edge gateways that track the health of the equipment for predictive maintenance. One extreme incident involved the main assembly robot producing inaccurate sensor readings that were altered, driving the robot to malfunction and claim weeks of expensive downtime on production. This revealed the insertion of an unauthorized device, a small single-board computer that was disguised as a sensor node and which fed erroneous data back to the control system.
CHALLENGES:[edit]
Even though it was optimized for efficiency, the factory edge network didn't include a device authentication protocol; attackers could access new sensors without the need for tight controls. Ensuring up time and keeping operational was prioritized often at the expense of timely application of security updates. Moreover, the presence of devices from many vendors further complicated efforts to establish consistent security standards, and production engineers received little training in cybersecurity best practices.
SOLUTIONS IMPLEMENTED[edit]
To solve these problems, stringent onboarding procedures were put in place: each sensor or controller must now present a digital certificate signed by the organization before being allowed onto the network. Any unknown device attempting to gain access is rejected and notification alerts are immediately sent out to ensure the remedying of bogus sensors does not take place in future. Additionally, they created a blockchain ledger to monitor device identities and to log any configuration changes over time. Every new addition or firmware update triggers a blockchain transaction being recorded to guarantee the creation of an immutable audit trail that can be reviewed by IT as well as OT (operational technology) teams increasing trust and accountability between departments. They segmented their network by listener and gateway: your sensors only talk to local gateway, and then your gateway only talks to central controls understanding that if any one part is breached there are limitations to how much of your network is attacked. More importantly, they rolled out an AI-powered detection system that monitored sensor readings for abnormalities. For known rogue sensors where outputs were statistically different from expected machine behavior; it is likely that ML models would have picked up on this irregularity early enough to allow for preemptive safety shutters before doing damage.In addition, maintenance processes were revised to ensure that scheduled downtimes were regular intervals of time explicitly dedicated towards security (for example, patching software vulnerabilities and routine equipment calibration checks). Training of staff on basic cyber hygiene such as ensuring that a USB drive or laptop was validated before connecting it into the organization edge networks have reduced the threat of the organization network being infected by malware.
OUTCOME[edit]
Then after enhancements made at this facility had enabled quick identification of anomalies; The next, an internal attempt by someone trying to connect using unauthorized monitoring tools was quickly detected and blocked ensuring nothing could affect operations in our pursuit against cyber-physical threats going forward. This includes how to properly secure our edges given their unique properties tightly coupled with how data generation happens right at the host itself which underlines an edge rather than left assume by further maintaining data access principles and protocols as logs have significantly aided audits of compliance as well being fitted into our own investigation processes during incidents reducing times taken before identifying potential problems where an immutable changelog was adapted into the process itself. Key Takeaways – Smart cities & IIOT factories share common challenges yet demonstrate needs for customized solutions & technologies but also show similar trends including segmentation, authentication continuous supervision Reacting quickly overcoming new challenges through advanced technology tools - Artificial Intelligence& Blockchain technologies just to name a few.
6.5 Open Challenges[edit]
Edge computing environments introduce a new paradigm of distributed intelligence, enabling real-time analytics, reduced latency, and improved bandwidth efficiency. However, this shift toward decentralized data processing exposes systems to novel privacy and security risks. Below, we present a comprehensive examination of persistent and emerging challenges, grounded in both theoretical studies and real-world implementations.
Scalability and Heterogeneity of Edge Devices[edit]
Edge ecosystems encompass a broad spectrum of devices—from powerful gateways to ultra-low-power sensors—resulting in inconsistent security postures.
Security Gap: The absence of unified standards for device identity, firmware updates, and runtime protection leads to fragmented security implementations. Some devices lack even basic encryption capabilities due to power or size constraints.
Research Insight: A 2021 IEEE survey highlighted that over 60% of IoT vendors lacked lifecycle security support for their devices, increasing the attack surface in large-scale deployments.
Real-World Case: The Barcelona Smart City project revealed multiple attack vectors in public infrastructure (e.g., street lighting and traffic signals) due to inconsistent device management and outdated firmware.
Ensuring Data Privacy Under Resource Constraints[edit]
Edge devices often collect and process highly sensitive data—such as biometric readings, location histories, and video footage—with limited hardware resources.
Core Tension: Algorithms such as federated learning or homomorphic encryption protect user data but demand substantial computational and memory resources, which are scarce on many edge devices.
Academic Observation: Studies by NIST and Stanford University show that naive deployment of privacy-preserving methods without edge-optimized variants significantly impairs performance and energy consumption.
Case Study: Intel’s OpenFL framework aimed to train healthcare models across hospitals using federated learning, but faced challenges in synchronizing updates and maintaining acceptable inference latency on edge-based medical imaging devices.
Trust Management in Dynamic and Unstable Topologies[edit]
Edge environments are inherently dynamic. Devices frequently join or leave the network, creating discontinuities in the chain of trust.
Problematic Assumption: Conventional security models assume static device identity and pre-established trust channels, which do not scale to highly mobile or intermittently connected edge nodes.
Emerging Solutions: Research in self-sovereign identity (SSI) and distributed ledger technologies offer promise, but current solutions suffer from scalability issues and latency concerns.
Case Study: The Egyptian Smart City Pilot attempted to use blockchain to verify edge node firmware, but trust propagation across newly added sensors failed under high churn conditions, causing delays in policy enforcement.
Attack Detection, Incident Response, and Autonomy[edit]
Edge systems often function autonomously with limited supervision, making attack detection and mitigation more difficult.
Key Risk: AI-driven anomaly detection systems require historical data and ongoing telemetry, which may not be available in disconnected or low-bandwidth deployments.
Operational Limitation: Many edge devices lack secure logging or rollback mechanisms, making it difficult to verify the root cause of incidents or recover quickly.
Case Study: At the University of Twente, a testbed for Industrial IoT systems showed that edge devices exposed to physical tampering could not escalate alerts promptly due to weak local intelligence and intermittent connectivity.
Isolation in Multi-Tenant Environments[edit]
As edge nodes begin to serve multiple stakeholders—such as different companies or applications—ensuring isolation becomes a critical security concern.
Challenge: Multi-tenancy can introduce covert channels, side-channel attacks, and privilege escalation opportunities if containers or VMs are not adequately separated.
Security Audit Findings: Research from Princeton showed that containerized edge workloads often shared CPU caches, allowing timing attacks to leak private information between tenants.
Case Study: In a real deployment by AT&T’s OpenStack Edge, researchers uncovered lateral privilege escalation opportunities due to default Kubernetes settings that lacked adequate network policy enforcement.
Regulatory Ambiguities and Compliance at the Edge[edit]
Data processed at the edge may cross jurisdictional boundaries, creating legal complexities regarding data ownership, sovereignty, and compliance.
Legal Blind Spots: Current regulations such as GDPR or HIPAA are largely designed for centralized cloud architectures, making it unclear how data localization and consent tracking apply in edge federations.
Example: Edge-based systems in autonomous vehicles collect vast location and behavioral data. Without clear guidelines, it is unclear which laws apply when data crosses borders in real-time.
Case Study: A European Telemedicine Consortium faced compliance challenges when processing patient data across edge nodes in different EU countries. The project was delayed for over a year due to unresolved questions around cross-border consent and retention policies.
Secure Firmware Updates and Lifecycle Management[edit]
Edge devices are often deployed in inaccessible locations for long periods, making remote patching essential—but risky.
Security Concern: Malicious actors could intercept or spoof over-the-air updates, leading to bricked devices or persistent backdoors.
Insufficient Tools: Many embedded devices lack secure boot or digital signature verification mechanisms to confirm update authenticity.
Case Study: The infamous Mirai Botnet exploited thousands of edge devices, including DVRs and routers, with outdated firmware and hard-coded credentials, highlighting the urgent need for secure firmware lifecycle practices.
Latency vs. Security Trade-offs in Time-Sensitive Applications[edit]
Mission-critical applications like autonomous vehicles, remote surgeries, and smart manufacturing require ultra-low latency. However, robust security checks often add processing delays.
Engineering Dilemma: Advanced encryption, identity verification, and behavioral monitoring all introduce latency that may be unacceptable in real-time control loops.
Case Study: A MIT study on drone navigation found that encrypting visual data and command signals caused 300–500ms latency, which made obstacle avoidance unreliable and led to system failures during high-speed flight.
Human-Centric Vulnerabilities and Misconfiguration Risks[edit]
Technological defenses alone are insufficient if human operators make configuration errors, fail to apply patches, or are vulnerable to social engineering. Soft Target: Maintenance staff or third-party vendors often access edge devices without adhering to strict security protocols. Case Study: A post-incident audit of Amazon Locker systems embedded with AI modules revealed unauthorized firmware uploads enabled via unmonitored USB ports. The issue stemmed from improperly trained field agents who bypassed signed update checks for convenience.
Citations[edit]
Y. Xiao, Y. Jia, C. Liu, X. Cheng, J. Yu and W. Lv, "Edge Computing Security: State of the Art and Challenges," in Proceedings of the IEEE, vol. 107, no. 8, pp. 1608-1631, Aug. 2019, doi: 10.1109/JPROC.2019.2918437. keywords: {Edge computing;Servers;Task analysis;Security;Cloud computing;Mobile handsets;Computer science;Smart phones;Internet of Things;Network security;Data security;edge computing;Internet of Things;network security},