Chapter 6: Edge Security and Privacy: Difference between revisions
Ali Siddiqi (talk | contribs) |
|||
| Line 50: | Line 50: | ||
==6.2 Data Privacy and Compliance in Edge Applications== | ==6.2 Data Privacy and Compliance in Edge Applications== | ||
===Privacy Issues in Fog Computing=== | |||
====Attack Vectors==== | |||
---- | |||
Below are some of the major attack vectors that plague existing edge and fog networks. | |||
; Forgery | |||
:Forgery is a security threat where the attacker copies someone else's identities and behavior by producing fake information. This is a serious issue that degrades existing network resources for everyone in the network. | |||
;Tampering | |||
: Attackers alter data that is to be sent to other websites. This is difficult to detect since users in an edge environment are mobile and we can't differentiate if the data has been tampered with or anomalous behavior is due to packet loss. | |||
;Spam | |||
:Attackers send fake information that overwhelms the processing power of the edge devices. Similar to DoS, on a smaller scale. | |||
;Sybil | |||
:Attackers fake identity to control the performance of edge network. Falsifying their identity allows them to create fake crowdsensing reports, which affects the reliability of the whole network. | |||
;Jamming | |||
:Attackers generate large amounts of packets to jam transmission channels and occupy important resources | |||
;Eavesdropping | |||
:Attackers listen to confidential data of genuine users from transmission channel by pretending to be a part of the network | |||
; Man in the Middle (MITM) | |||
: MITM is a type of cyberattack where the attacker not only eavesdrops on communication between two devices, but also modifies the payload for destructive payloads. | |||
;Collusion | |||
:Multiple groups band together to mislead fog nodes | |||
;Impersonation | |||
:Attacker acts as real server to trick users to steal all their data | |||
;Virtual Machine Attack | |||
:Attackers take control of hypervisor for the virtual machine's VM | |||
;Side channel | |||
: Attackers brute force passwords to steal information being shared between two parties. Due to the poor resource availability of edge devices, there is a constraint on the use of computationally expensive hashing algorithms. | |||
; Session Hijacking | |||
: Attackers intercept and steal user session to get access to confidential data | |||
==== Privacy Issues in Fog Computing ==== | |||
# User privacy | |||
## fog computing contains large number of IoT devices that are inter-connected via sensors | |||
## generated senesitive data and transmit to fog nodse for processing. This sensitive data includes personal information which can be stolen | |||
# Identity Privacy | |||
## ID of users is extremely vulnerable of getting disclosed while having auth to nodes including name, phone , address | |||
# Data Privacy | |||
## data can be exposed to network attacker who is trying to steam user's personal data from the transmission medium or relay nodes | |||
# Usage privacy | |||
## Pattern in which accesses services of fog computing | |||
## intruder knows when user is accessing the channel for data transmission and when he is not communicating | |||
## intruder attacks on user's confidential information or the channel | |||
# Location Privacy | |||
## location privacy helps attackers know the trajectory of the user | |||
# Network Privacy | |||
## wireless connections always at risk | |||
## maintenance of fog nodes is challenging since they are present at edge of internet | |||
## privacy breach is not difficult to occur | |||
=== Security and Privacy issues for edge computing=== | |||
# nodes of edge connected to large number of IoT | |||
## these have limited resources | |||
## heterogeneous internal components | |||
## Key management for ensuring privacy of data is difficult | |||
==== Issues ==== | |||
# Edge nodes are near to users which makes large amount of sensitive data, which might be stolen | |||
# Edge computing possess low network resources so doesn't support expensive encryption algos | |||
# Edge environment consists of dynamic env which is changing, which allows attackers multiple ways to join the network | |||
ALso difficult to create securiy rules for a changing network | |||
==== Attacks ==== | |||
; Eavesdropping: Monitor channel to steal data | |||
;# DoS | |||
: take control of network by sending fake requests | |||
;# DDoS | |||
: interrupt normal services provided by different servers | |||
;# Data Tampering | |||
: Attacker can alter the data transmitted over comm channel | |||
;False data injection | |||
:Attacker injects false code in network which brings all data to the attacker | |||
;Physical attack | |||
:Physical protection of edge infra is weak, which allows attackers to compromise the physical locations of edge devices. | |||
; Rogue gateway | |||
:inject large amounts of traffic into edge network infra, similar to MITM | |||
==== Privacy issues in edge computing ===== | |||
# weak security techniques for system protection | |||
# unsafe communication between devices | |||
# difficult recovery and data backup | |||
# no specific pattern of update reception | |||
# lack of proper network visibility | |||
# lack of user's selective data collection | |||
==== Countermeasures for Fog Computing ==== | |||
;Efficient encryption techniques | |||
:Allows for resource constrained edge devices to encrypt communcations with complex algorithms | |||
;Decoy technique | |||
:Authenticate data of user present the computing network by replacing original information with fake information that is provided to attackers | |||
When breached, the attackers find the decoy files | |||
;Intrusion detection system | |||
:Detect and protect from attacks including DoS, insider attackers, port scanning attacks, flooding attacks on virtual machine, MITM | |||
;Blockchain security for fog computing | |||
:Blockchain is a way to cryptographically ensure the validity of a system while simultaneously increasing it's security. Using blockchain for edge computing reduces single point failure, increases network security and helps with tracking node status effectively. | |||
==6.3 Security Protocols and Frameworks for Edge Systems== | ==6.3 Security Protocols and Frameworks for Edge Systems== | ||
Revision as of 05:16, 7 April 2025
6. Edge Security and Privacy
6.1 Overview of Security Challenges in Edge Computing
From previous chapters, Edge Computing has shown that it is here to stay and it will keep rapidly growing throughout the years. However, Edge Computing has its own security challenges that have to be addressed, because it is not a perfect system. Edge Computing has many security challenges that have to be dealt with in order to keep data safe. In this section, we will be talking about the different kinds of attacks that can happen on an Edge server or device, as how they are able to do this.
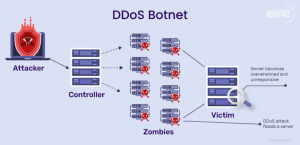
DDoS
DDoS is a type of cyberattack in which an attacker aims to disrupt services provided by one or more servers based on distributed based on distributed resources such as a cluster of compromised Edge devices, which are also known as botnets. DDoS attacks occur when an attacker persistently sends streams of packets to a victim from compromised electronic devices, which causes the hardware resources of the victim to be quickly exhausted by handling these malicious packets and can no longer process any legitimate request on time. There are two kinds of DDoS attacks: Flooding-based and Zero-day DDoS attacks.
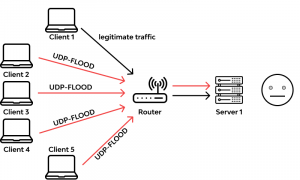
Flooding-based DDoS attacks are a type of of DDoS attacks aiming to shut down normal service of a server based on large amount of flooded malformed or malicious network packets and are mainly classified as UDP flooding, ICMP flooding, SYN flooding, ping of death (PoD), HTTP flooding, and Slowloris.
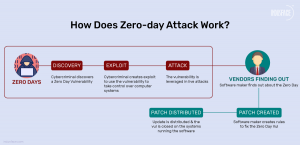
Zero-Day DDoS attacks are when an attacker must find an unknown vulnerability in a piece of code running on the target Edge server or device, which can cause memory corruption and finally result in a service shutdown. For example, newly built Edge servers could have code vulnerabilities, such as a hanging pointers or stack overflows, and an attacker can abuse those vulnerabilities in order to cause the Edge servers or devices to overload due to memory issues and shut down.
Side-Channel Attacks
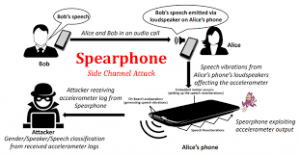
Side-Channel Attacks happen when an attacker constantly obtains certain side-channel information, like using public information that is not privately-sensitive for a user, from the target edge computing infrastructure and then feeds it into specific algorithms or machine learning models that outputs the desired sensitive information. There are three kinds of Side-Channel attacks: attacks exploiting communication channels, attacks exploiting power consumption, and attacks exploiting smartphone-based channels.
Attacks exploiting communication channels are when an attacker can use a malicious node, that doesn't have to be an edge server or device, in order to exploit communication channels and uses the node to continuously sniff the network traces and wishes to extract sensitive information out of them. Attacks exploiting power consumption are when attackers use smart meters and oscilloscopes in order to measure the power consumption of a system since it carries information related to either the device that consumes the energy as different devices have different power. Attacks exploiting smartphone-based channels are when attackers exploit vulnerabilities using /proc and smartphone embedded sensors due to how sensors can leak information and send malware to the user that they can install but disguised as something important and attack /proc.
Malware Injection
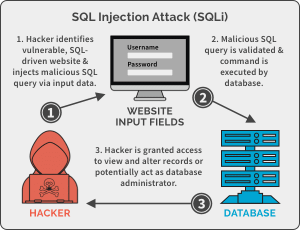
Malware Injection is when an attacker injects malicious code, or malware, into edge devices or servers and is classified as either server-side or device-side injections. Server-side injections are separated into four types: SQL, XSS, CSRF and SSRF, and XML. Device-side injection is when an attacker injects the malware directly into IoT devices since IoT devices are highly heterogeneous, so an attacker can physically inject or use third-party malicious libraries that are powerful and less likely to get detected.
SQL injection is a code injection technique that attackers can use in order to destroy back-end databases by using the SQL query and escape sequences to trick the server into thinking the code is valid. XSS injection is a client-side attack in which an attacker injects malicious code into data content, which can be accessed and executed automatically by the servers. CSRF injection is an attack in which an end user is forced to execute unwanted actions through Web applications. SSRF injection is an attack in which Edge servers are abused to read or alter the internal resources. XML injection is an attack which an attacker intercepts an XML message and edits with malicious code so that it is sent to the Edge servers using Simple Object Access Protocol (SOAP).
Authorization and Authentication Attacks
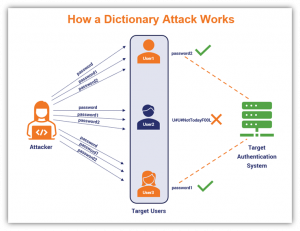
When these attacks happen, an attacker can bypass authentication processes and gain unauthorized access by using four techniques: dictionary attacks, attacks exploiting vulnerabilities in authorization protocols, attacks exploiting vulnerabilities in authorization protocols, and overprivileged attacks.
Dictionary attack is when an attacker possesses a dictionary containing the most used credentials or passwords and inputs all possible entries in this dictionary in order to brute force a match. Attacks exploiting vulnerabilities in authorization protocols are when attackers look for design flaws in how authentication protocols are being used, like finding vulnerabilities in WPA2 or WPA3 protocols which can give an attacker messages that have encrypted information. They can also use 4G or 5G vulnerabilities in order to find a person's location and inject fabricated paging messages to mess with them and gain more information. Attacks exploiting vulnerabilities in authorization protocols are when attackers look for flaws in how authorization protocols are designed, such as an attacker using vulnerabilities in OAuth single sign-in which let them access victims personal information without authorization. Overprivileged attacks are when attackers are able to develop malicious apps that can do things that they do not have permission to do without needing to authenticate, such as changing door pins and setting off fire alarms in a house.
How are attackers able to perform these attacks?
Attackers are able to attack Edge devices or servers using different attack techniques, but it is more than just that. Attackers are able to abuse vulnerabilities and flaws in the Edge systems, specifically protocol-level design flaws, implementation-level flaws, code-level vulnerabilities, data correlations, and lacking in fine-grained access controls.
Protocol-level design flaws are caused by many protocols edge computing having adopted design flaws due to their designers mainly focus on utility and user experience rather than not providing security as well. Implementation-level flaws are logic flaws that can cause security strength to decrease significantly after being proved that it was strictly secure on paper, because developers may misunderstand the foundations of the protocol and migrating a protocol from other platforms to the edge computing platform may cause adaptivity inconsistency. Code-level vulnerabilities can be system bugs that cause memory failure or corruptness, like stack or heap overflow, and can be caused when a person is programming millions of lines of code but leaves something like a dangling pointer. Data correlations is caused when there could be hidden correlations between sensitive and insensitive data that edge produces that might not be straightforward to notice, which an attack can abuse using side-channels. Lacking in fine-grained access controls means that Edge computing systems cannot implement fine-grained access controls, because it cannot be adapted to edge computing due to the more complex and fine-grained permissions scenarios, making it easier to attack edge systems.
Overall, the Edge security challenges can be avoided if there was more attention to the potential vulnerabilities or flaws. In the next sections, they will talk about data privacy on Edge systems, security protocols that Edge systems use to combat attacks on their systems, and real cases about actual security breaches that happened on the edge.
6.2 Data Privacy and Compliance in Edge Applications
Privacy Issues in Fog Computing
Attack Vectors
Below are some of the major attack vectors that plague existing edge and fog networks.
- Forgery
- Forgery is a security threat where the attacker copies someone else's identities and behavior by producing fake information. This is a serious issue that degrades existing network resources for everyone in the network.
- Tampering
- Attackers alter data that is to be sent to other websites. This is difficult to detect since users in an edge environment are mobile and we can't differentiate if the data has been tampered with or anomalous behavior is due to packet loss.
- Spam
- Attackers send fake information that overwhelms the processing power of the edge devices. Similar to DoS, on a smaller scale.
- Sybil
- Attackers fake identity to control the performance of edge network. Falsifying their identity allows them to create fake crowdsensing reports, which affects the reliability of the whole network.
- Jamming
- Attackers generate large amounts of packets to jam transmission channels and occupy important resources
- Eavesdropping
- Attackers listen to confidential data of genuine users from transmission channel by pretending to be a part of the network
- Man in the Middle (MITM)
- MITM is a type of cyberattack where the attacker not only eavesdrops on communication between two devices, but also modifies the payload for destructive payloads.
- Collusion
- Multiple groups band together to mislead fog nodes
- Impersonation
- Attacker acts as real server to trick users to steal all their data
- Virtual Machine Attack
- Attackers take control of hypervisor for the virtual machine's VM
- Side channel
- Attackers brute force passwords to steal information being shared between two parties. Due to the poor resource availability of edge devices, there is a constraint on the use of computationally expensive hashing algorithms.
- Session Hijacking
- Attackers intercept and steal user session to get access to confidential data
Privacy Issues in Fog Computing
- User privacy
- fog computing contains large number of IoT devices that are inter-connected via sensors
- generated senesitive data and transmit to fog nodse for processing. This sensitive data includes personal information which can be stolen
- Identity Privacy
- ID of users is extremely vulnerable of getting disclosed while having auth to nodes including name, phone , address
- Data Privacy
- data can be exposed to network attacker who is trying to steam user's personal data from the transmission medium or relay nodes
- Usage privacy
- Pattern in which accesses services of fog computing
- intruder knows when user is accessing the channel for data transmission and when he is not communicating
- intruder attacks on user's confidential information or the channel
- Location Privacy
- location privacy helps attackers know the trajectory of the user
- Network Privacy
- wireless connections always at risk
- maintenance of fog nodes is challenging since they are present at edge of internet
- privacy breach is not difficult to occur
Security and Privacy issues for edge computing
- nodes of edge connected to large number of IoT
- these have limited resources
- heterogeneous internal components
- Key management for ensuring privacy of data is difficult
Issues
- Edge nodes are near to users which makes large amount of sensitive data, which might be stolen
- Edge computing possess low network resources so doesn't support expensive encryption algos
- Edge environment consists of dynamic env which is changing, which allows attackers multiple ways to join the network
ALso difficult to create securiy rules for a changing network
Attacks
- Eavesdropping
- Monitor channel to steal data
- DoS
- take control of network by sending fake requests
- DDoS
- interrupt normal services provided by different servers
- Data Tampering
- Attacker can alter the data transmitted over comm channel
- False data injection
- Attacker injects false code in network which brings all data to the attacker
- Physical attack
- Physical protection of edge infra is weak, which allows attackers to compromise the physical locations of edge devices.
- Rogue gateway
- inject large amounts of traffic into edge network infra, similar to MITM
Privacy issues in edge computing =
- weak security techniques for system protection
- unsafe communication between devices
- difficult recovery and data backup
- no specific pattern of update reception
- lack of proper network visibility
- lack of user's selective data collection
Countermeasures for Fog Computing
- Efficient encryption techniques
- Allows for resource constrained edge devices to encrypt communcations with complex algorithms
- Decoy technique
- Authenticate data of user present the computing network by replacing original information with fake information that is provided to attackers
When breached, the attackers find the decoy files
- Intrusion detection system
- Detect and protect from attacks including DoS, insider attackers, port scanning attacks, flooding attacks on virtual machine, MITM
- Blockchain security for fog computing
- Blockchain is a way to cryptographically ensure the validity of a system while simultaneously increasing it's security. Using blockchain for edge computing reduces single point failure, increases network security and helps with tracking node status effectively.
6.3 Security Protocols and Frameworks for Edge Systems
6.4 Case Studies: Real-World Security Breaches
Citations
Y. Xiao, Y. Jia, C. Liu, X. Cheng, J. Yu and W. Lv, "Edge Computing Security: State of the Art and Challenges," in Proceedings of the IEEE, vol. 107, no. 8, pp. 1608-1631, Aug. 2019, doi: 10.1109/JPROC.2019.2918437. keywords: {Edge computing;Servers;Task analysis;Security;Cloud computing;Mobile handsets;Computer science;Smart phones;Internet of Things;Network security;Data security;edge computing;Internet of Things;network security},